Phishing on the Opensea
Scammer used legitimate Opensea buy contract as a "blank check" to clean out victim wallets; stolen NFTs then sold using Opensea's platform
On February 9, 2021, an unidentified scammer used a phishing attack to steal dozens of NFTs from individual wallets. The NFTs were then rapidly sold via Opensea’s platform, netting the thief nearly 700 Ethereum (~$2 million). More stolen NFTs were sold via the LooksRare exchange and Sushiswap. In total, the scammer netted over 1100 Eth (~$3 million) from the attack.
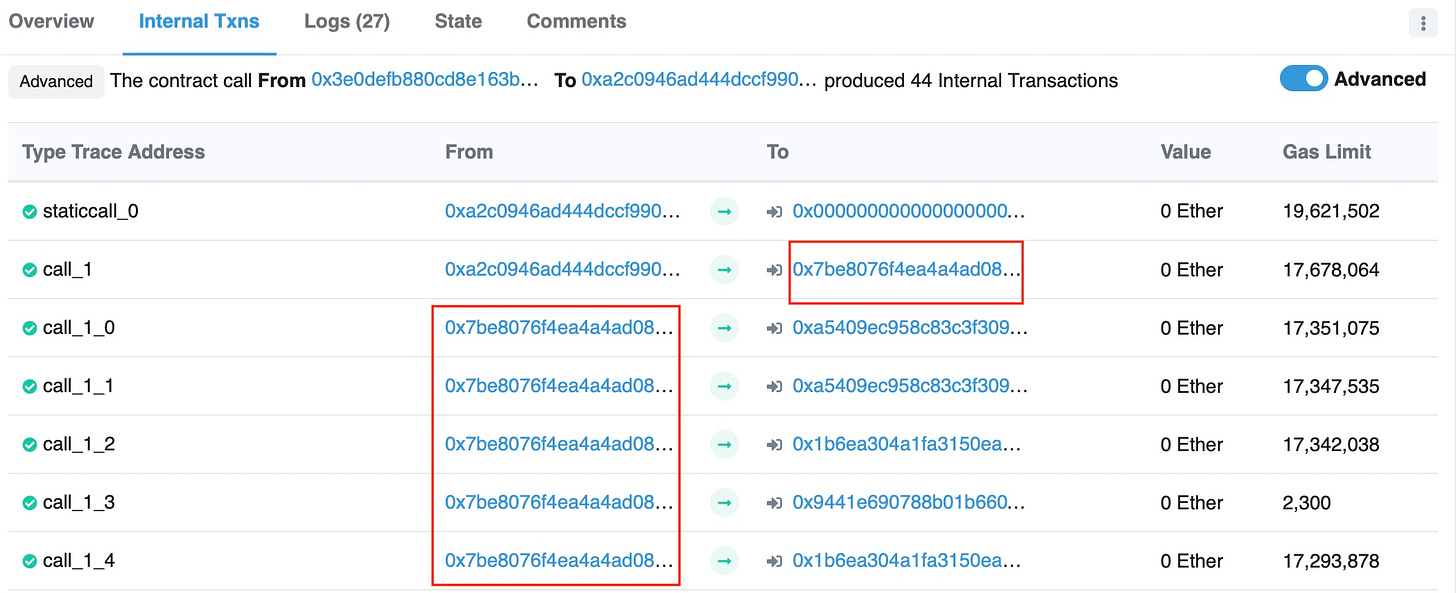
The phishing attack used a legitimate Opensea buy order. It is still unclear how this contract was delivered, but it likely came via a copycat email pretending to be from Opensea. Any individual who signed this order gave the thief permission to transfer NFTs to their wallet at zero cost:

The scam contract was created nearly a month prior to the attack:


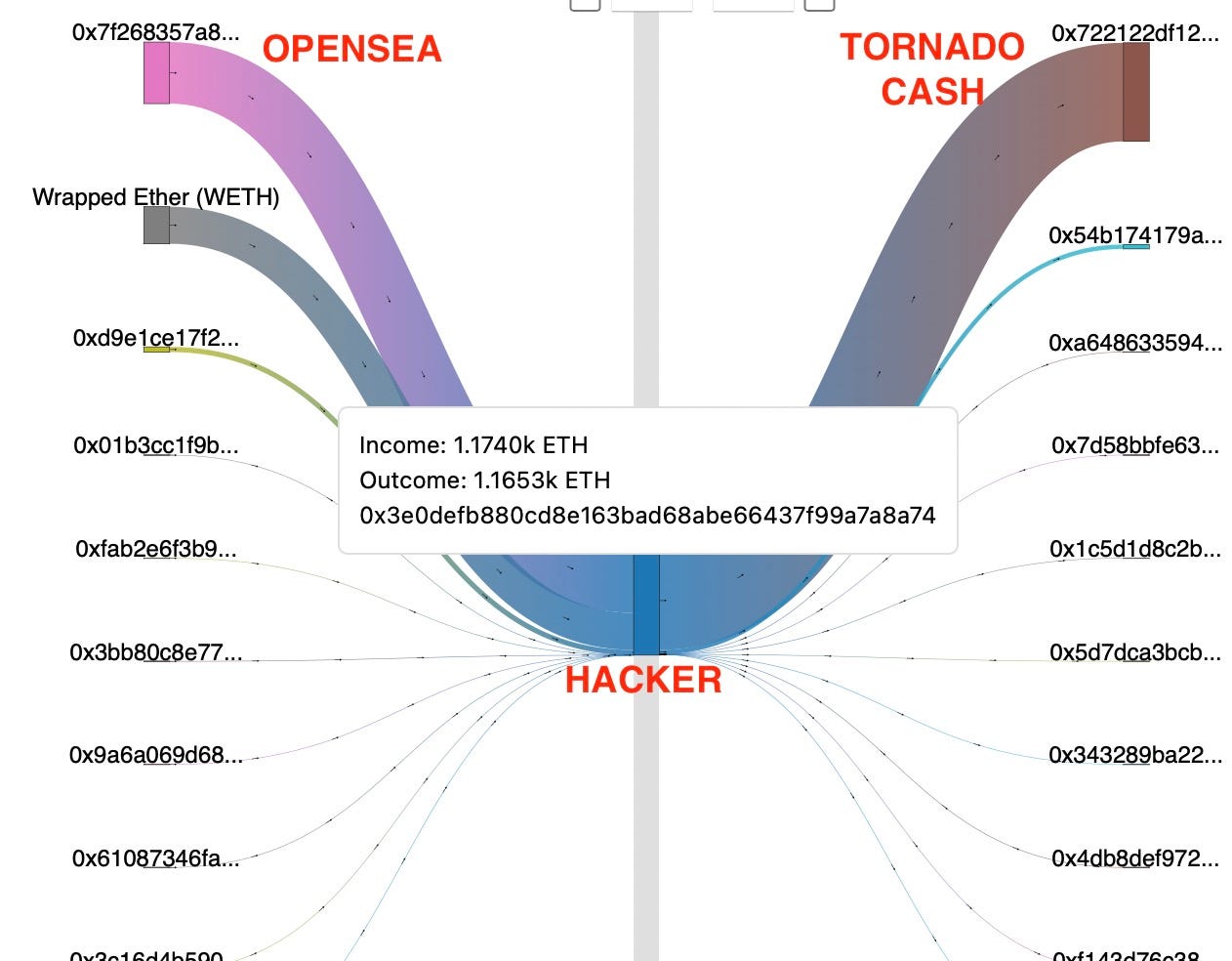
After initiating the attack, the scammer drained dozens of NFTs from the victim wallets. Many of the stolen NFTs were then sold on Opensea’s platform within hours of the theft, netting the scammer nearly 700 Ethereum:
Roughly 12 hours after intiating this attack, the scam wallet was identified and ceased transactions on Opensea. However, the scammer continued to sell several NFTs via Sushiswap and the LooksRare NFT platform. The scammer then elected to send the unsold NFTs back to the original owners. Strangely, the scammer also sent 50 Eth to one of the victims, naterivers.eth, who claims he does not know the reason for this transfer.
Finally, the hacker transferred the total proceeds from the illicit sales, some 1100 Ethereum, into the Tornado Cash mixer. Tornado Cash allows users to “wash” ethereum and prevent further tracking via the blockchain.*
Who is to blame?
There’s a lot of blame to go around. Since “code is law,” many people have argued that the blame rests solely on the victims shoulders. The victims of this attack signed a contract without reading it first. Opensea’s own initial statement stated that the attack “originated outside of Opensea’s website,” implying the responsibility for the losses rests with the victims.

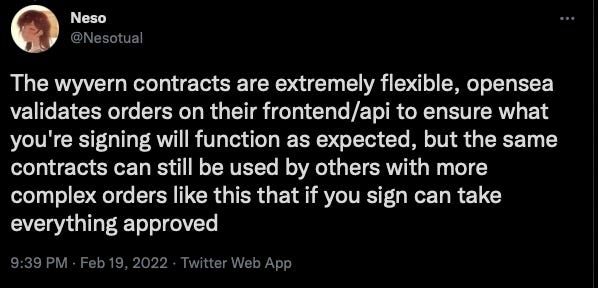
However, Opensea’s buy order enabled the scammer to design and implement a complex order without any oversight. Opensea’s contract was then directly used to steal these NFTs, meaning that without this vulnerability in Opensea, the hack never would have happened. Opensea also failed to detect warning signs related to the scammer’s wallet, including the fact that it was initially funded with a transfer from the Tornado Cash mixer.
Multiple people noted that there are minimal controls related to the design and implementation of Opensea buy orders, leaving the system vulnerable to this type of exploit:
After the theft, Opensea facilitated the sale of many stolen NFTs. Additionally, the Sushiswap and LooksRare platforms continued to allow the sale of stolen NFTs hours after the hack was identified and well-publicized. The purchasers of these NFTs are also victims; receiving stolen property is illegal and they should, in theory, be required to return these NFTs to the original owners.
We hope to see Opensea and LooksRare taking responsibility for their role in facilitating the sale of stolen property. We also hope that Opensea will implement additional controls to ensure that their order system cannot be exploited in this type of attack.
*Tornado Cash may not be invulnerable to tracking by law enforcement. Use at your own risk, scammers!




Where can I learn, know and read this Smart Contracts (anyone) ???? I want to say like, how? because I´m really interesting.
Amazing Information, good job! and thank by writting.
How can I learn to read a smart contracts and know it????